Symmetry | Free Full-Text | Machine Learning-Based Botnet Detection in Software-Defined Network: A Systematic Review
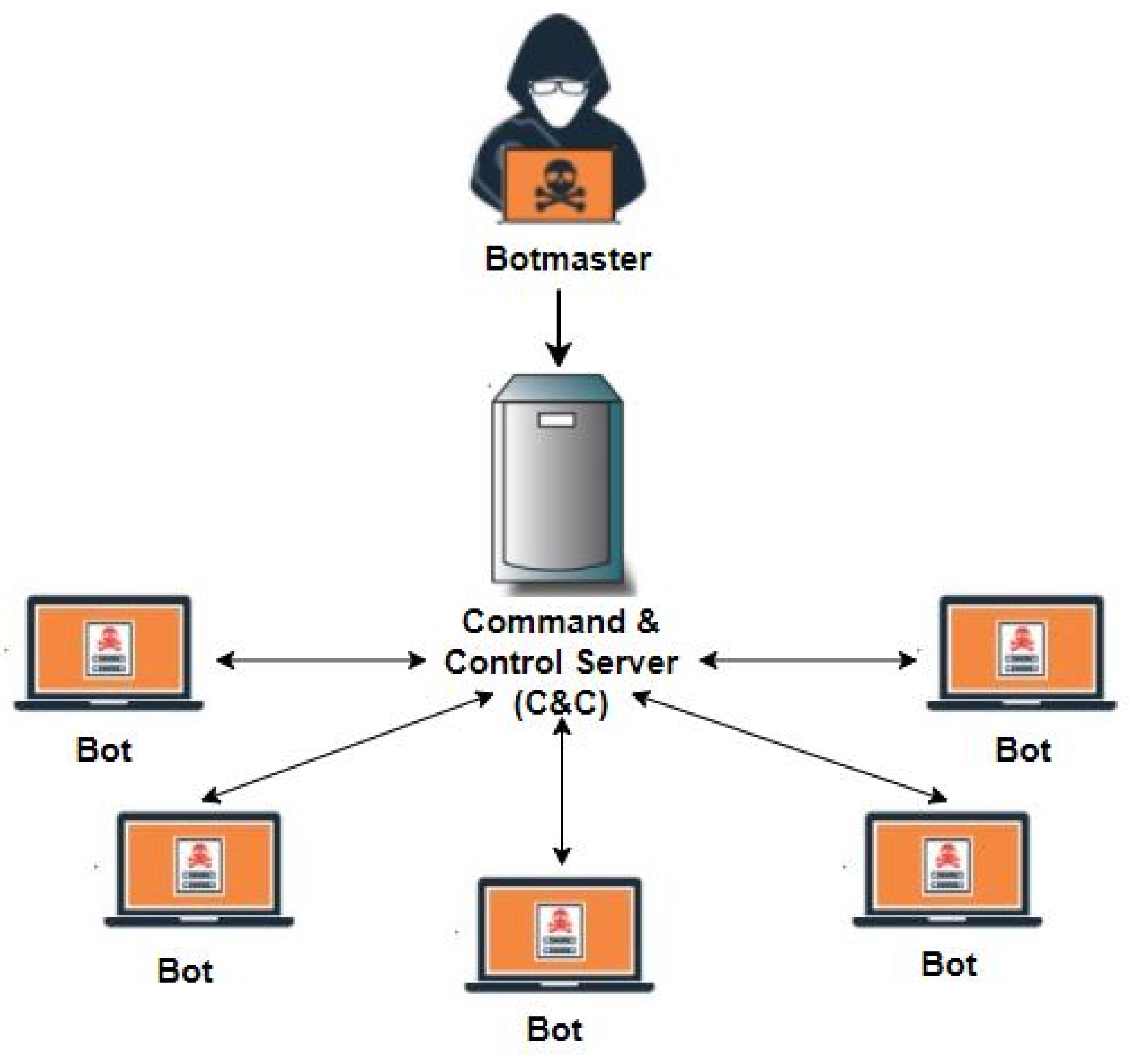
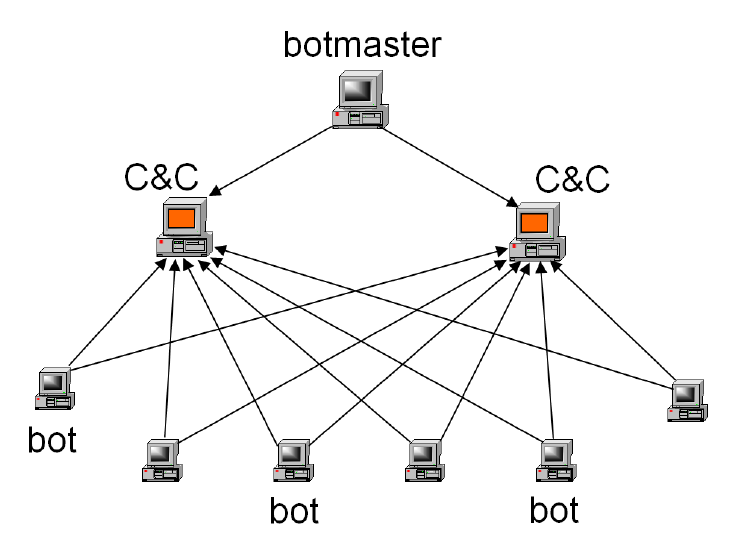
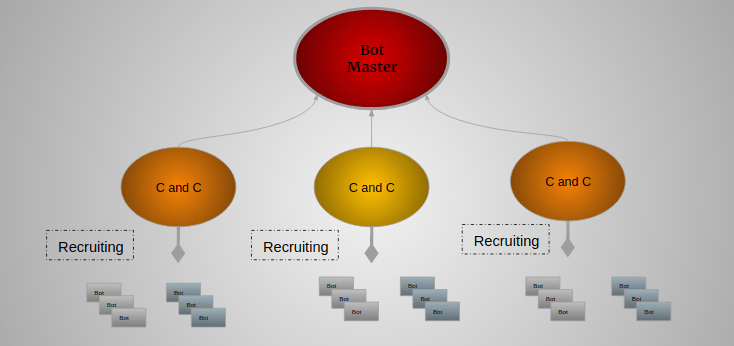
Basic entities of botnet: bots, command and control (C&C) server, and... | Download Scientific Diagram
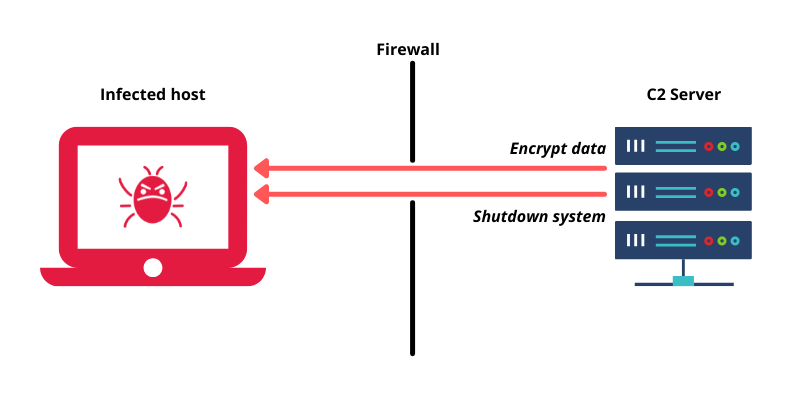
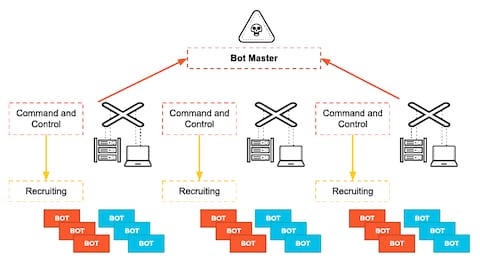
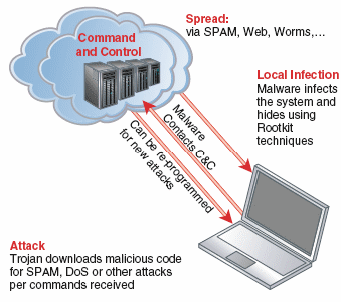
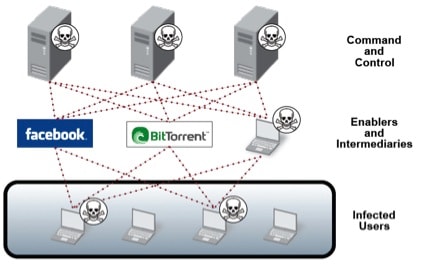
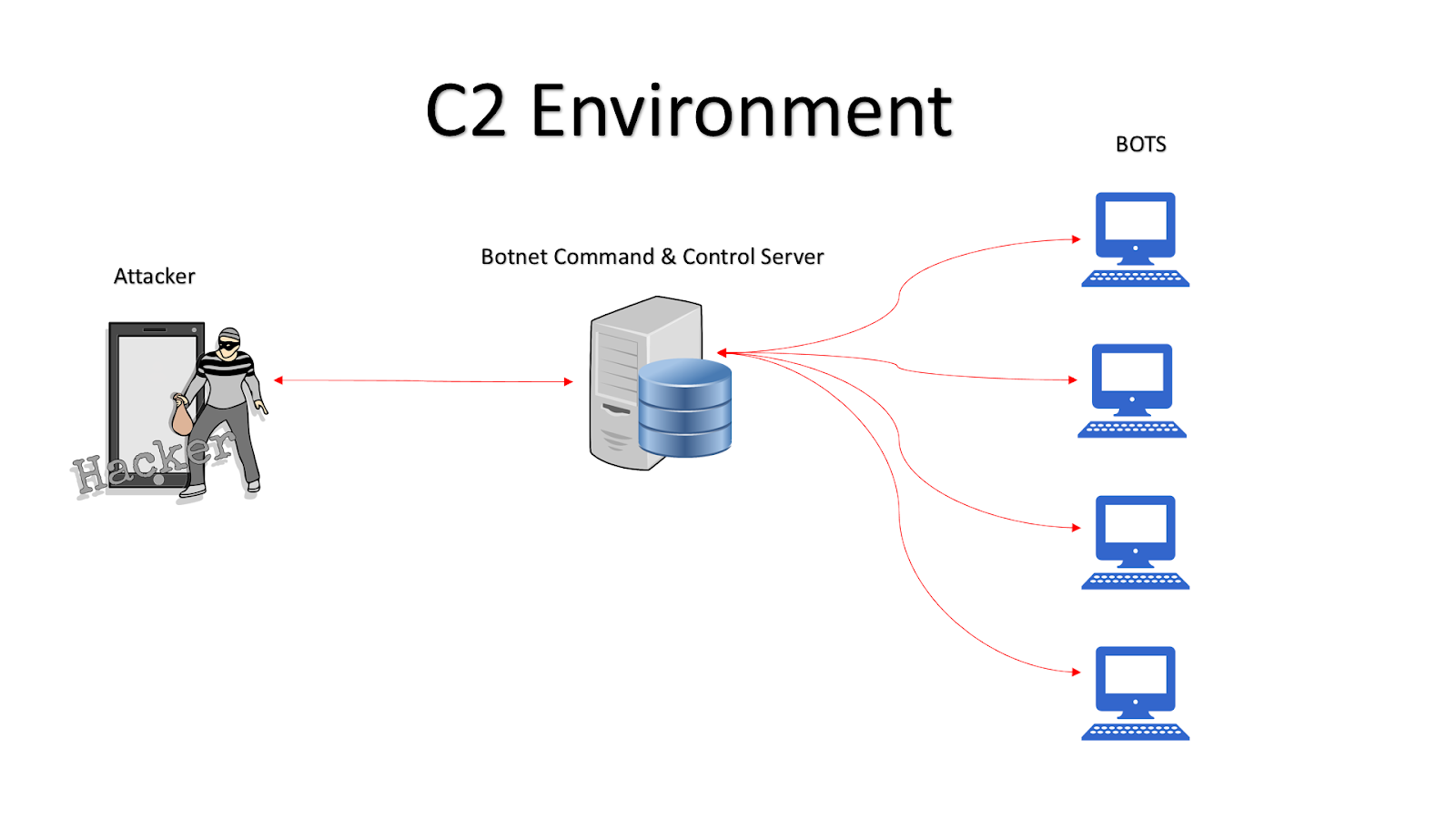
How a C2 Server is Leveraged in a Botnet Command and Control Attack | by Fikayo Adepoju | DNSFilter Blog | Medium